Phishing is a type of social engineering attack aimed at tricking users into revealing login details, payment information, and other sensitive data. It occurs when an attacker, pretending to be a trusted entity, convinces a user to click on a harmful link or download a malicious file. This can be done through various channels such as emails, text messages, phone calls, or social media. Fall for such a scam, and you could be in for a firestorm of malware infections, system slowdowns, and loss of sensitive data, among other issues.
As you’ve probably noted from the news over the last few years, the repercussions of these attacks can be devastating. On a personal level, you may find yourself endlessly disputing unauthorised purchases, fighting financial fraud, and possibly even struggling with identity theft. If it’s your business that’s compromised, you may face significant financial losses. You’ll likely also experience a drop in market share and reputation, leading to a loss of trust among stakeholders.
It can be incredibly hard to claw your way back from such catastrophic losses. And unfortunately, phishing attacks are showing no signs of going out of fashion. On the contrary, the attack vector is growing more sophisticated and more frequent with each passing day.
The rise of remote and hybrid work models has contributed to this increase in scam emails, with multiple mobile endpoints equating to multiple vulnerabilities that can be leveraged by attackers. Organisational oversights are also closely linked to phishing attacks. Companies that fail to invest in cyber security and staff training are at a greater risk of opening the door for cybercriminals.
On top of these internal issues, there’s the ever-evolving sophistication of cybercriminals and the increasing availability of affordable phishing tools supplied via the dark web.
How can you stay safe and avoid phishing attacks?
To avoid falling victim to phishing, it’s crucial to remain constantly vigilant whenever you’re connected to the internet. To keep yourself and your business safe, you must:
1. Be Cautious of Suspicious Messages
Here, it’s important to note that phishing extends beyond the realm of emails. Though your inbox certainly is one of the biggest danger zones, it’s crucial to understand that phishing attacks can come via many other vectors. These are the main ones to look out for:
- Smishing (SMS Phishing): Scam text messages designed to trick you into divulging sensitive data.
- Social Media Phishing: Similar to Smishing, but the attackers use social media platforms like Facebook, LinkedIn, or Instagram to trick you into providing sensitive information.
- Vishing (Voice Phishing): Phishing over the phone, via voice email, or using VoIP (voice over Internet Protocol) calls.
- Spear Phishing: A targeted phishing method where criminals impersonate a trusted source to steal your data.
- HTTPS Phishing: Cybercriminals trick you into giving up personal data using a malicious website.
- Pharming: Scammers install malicious code on a computer or other device to redirect the user to fake websites.
- Website Spoofing: Attackers create a fake website to collect your personal information.
- Search Engine Phishing: Attackers create a fake webpage that is indexed by genuine search engines.
- Man-in-the-Middle (MITM) Attacks: An attacker intercepts (and possibly alters) messages between parties who believe they are communicating with each other directly.
- Email Phishing: The most common phishing variant, this method will appear in your inbox. The attacker will pose as someone legitimate in hopes that you’ll reveal sensitive information.
With so many potential attack vectors, the sad truth is that you need to be vigilant whenever you’re using a device connected to the internet. Get into the habit of checking the sender’s address whenever you receive a message. More importantly, get used to spotting fakes.
Here are a few email address examples to test your skills on:
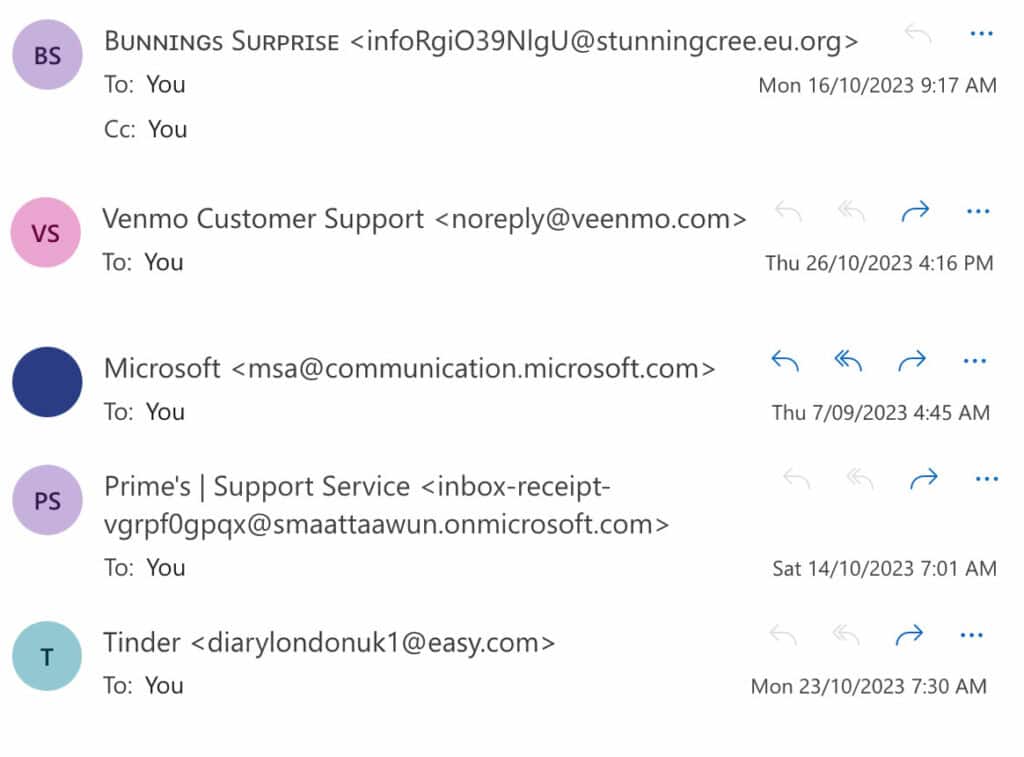
Can you spot the real address among the fake ones? Some of the fakes are pretty obvious. After all, no legitimate business is going to contact you from an email address that looks like it’s been in a wrestling match with the alphabet.
The Venmo one is a little trickier as your mind might skip over that second e in the email address. Interestingly, the Microsoft address – which was the only legitimate one – might make you pause for a moment since it’s a little unusual. In such cases, a quick Google search of the address should reveal right away whether it’s safe or not.
2. Never Click Unverified Links
Links in emails and other messages can lead to malicious websites designed to steal your information. The tricky part is that these links often come packaged with an urgent message designed to make you click before you think. So, get into the habit of pausing before clicking any links you’re not 100% sure about.
If you’re feeling suspicious, you can take a look at the URL by right-clicking the hyperlinked text and clicking “Copy Link Address”. Then paste the URL into an empty Google doc or your preferred notes app. By doing this, you can check that the link genuinely goes to the website it says it does. If it looks like the right website at a glance, don’t paste it into your browser right away. Instead, look for misspellings (e.g. amazons.com instead of amazon.com) that could indicate a malicious website.
3. Use Multi-Factor Authentication (MFA)
Let’s say the worst-case scenario happens and you enter your login details into a fake website. This could end up being a non-event if you have multi-factor authentication in place.
MFA involves using things like secret questions, authenticator apps, or messages sent to your phone or email account to verify login. With MFA in place, even if a phisher gets your password, they won’t be able to access your account without the second factor. You’ll still need to change your password if you’ve given up your login details. But at least the attackers won’t have gotten anything of value from you.
4. Keep Your Devices and Software Updated
Maintaining up-to-date IT infrastructure is paramount in safeguarding your systems against hackers who prey on outdated or unpatched systems. Regular software updates will ensure you’re getting the newly released patches needed to rectify security vulnerabilities, thereby offering protection against known threats. To ensure consistent security, enabling automatic updates is highly recommended.
Of course, you may have heard about cyberattacks in which ransomware was delivered to clients via official-looking updates. While this is a rare occurrence, it still pays to be able to tell the difference between real and fake software and app updates. We’ve got you covered on this front – check out our guide to spotting fake software updates.
While updates are essential, it’s also crucial to strategically isolate critical infrastructure components. This approach ensures a breach in one area doesn’t trigger a domino effect, causing your entire system to collapse. To further bolster your defences, consider deploying an automated phishing detection solution. Leveraging the power of artificial intelligence, such solutions can provide an additional layer of security, effectively identifying and mitigating phishing threats.
5. Educate Yourself and Your Team on Phishing Scams
Keeping yourself updated on the latest phishing techniques and disseminating this information to your team can significantly reduce your likelihood of falling prey to phishing attacks. To ensure a unified understanding and adherence to security protocols, facilitate regular security training sessions. These sessions will not only foster a culture of vigilance but also ensure employees comply with relevant security requirements.
As essential as training is, your security awareness initiatives can’t end there. Shockingly, some of the world’s most renowned tech companies have been hit with successful phishing attacks. Staff education was not the missing factor in these cases. Rather, the missing link was ongoing drills to lock this information into everyone’s minds.
You can avoid this mistake by conducting random phishing drills throughout the year. Doing so should provide invaluable insights into the alertness level of your employees. These drills serve as practical tests of the effectiveness of your training sessions and help identify areas that may require additional focus.
While phishing attacks are becoming increasingly sophisticated, these tips can help you reduce your risk of becoming a victim. Stay vigilant, stay informed, and stay safe out there in the wilds of the internet. Most importantly, remember that security is not a product but a process.
If you could use some help ensuring your cybersecurity products and processes are up to scratch, Invotec is your answer. We have multiple teams of IT experts, each specialising in different industries. This means we can set you up with consultants who understand your business and the digital strategy needed to help you thrive. Contact us today for a commitment-free discussion.